By Daniel Jackson
News Editor
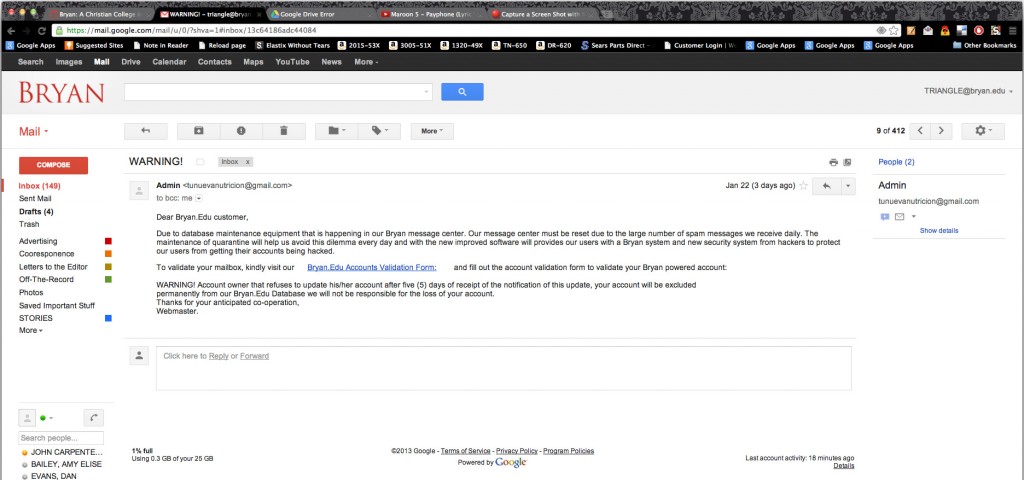
About 200 Bryan.edu email accounts were recipients of a phishing attempt Jan. 22.
The email claimed that it was the Admin for the Bryan.edu account, asking for users to “validate” their email accounts.
The email said, “Due to database maintenance equipment that is happening in our Bryan message center. [sic] Our message center must be reset due to the large number of spam messages we receive daily.”
The email included a link to a Google document which asked the users for their name, address, birth date, username and password.
Director of IT Services Steve Paulson said he knows of only one person who filled out the information, who then asked IT for help resetting his or her password.
The college is not in any more danger than it was before the phishing incident, Paulson said.
“The main security weakness in any social engineering attack are users who are not discerning, cautious, or savvy enough to recognize a phishing attempt and simply delete it,” he said.
Most of the accounts that received the message were faculty and staff members.
“Few—if any—students received the phishing message,” Paulson said.
Within five minutes of receiving the message, Paulson sent a message to faculty and staff, distributed by the Office of the President, warning them of the phishing attempt. Within an hour, he sent a message to everyone on the bryan.edu domain about the scam.
Paulson used the “report abuse” tab at the bottom of the Google document to notify Google of the scam.
Although Paulson does not know who sent the message—he’ll leave that for Google to figure out—he said the phisher probably tried to gain access to an account–anyone’s account–and from there, look to see what documents and network access the person has.
“If the account is associated with other services or accounts,” Paulson said, “(online shopping, banking, social media accounts, etc.) the phisher could use “forgot password” links to potentially gain access to other accounts and resources belonging to the phishing victim.”
Paulson said the phishing scam was not very complex.
Bryan has to deal with phishing scams a few times every year. Most of the time, users will contact IT to notify it of a phishing scam or to ask if the email is legitimate.
“It (the emails on Jan. 22) was a phishing attempt that was targeted at the low-hanging fruit on our domain,” Paulson said. “i.e., a list of email addresses that was obtained through little effort in hopes of gaining access to accounts and/or the personal information of at least some of the targeted individuals.”


